之前写过一篇fastjson漏洞文章,但是当时在复现利用链的过程中一直没有弹出计算器,而且利用链的代码单步调试也没有给出来,这次我要通过底层代码把漏洞实现过程展现出来。,上次不是没有弹出计算器吗,这次我先把可以弹出计算器的漏洞demo先讲解一下。,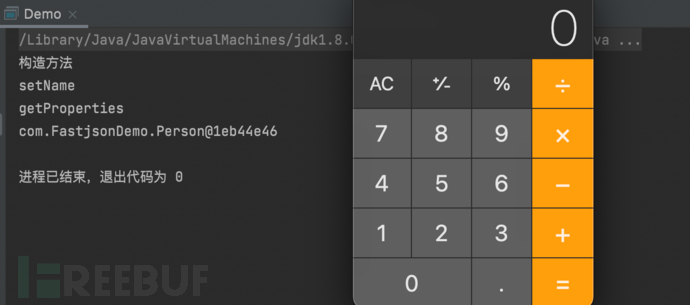 1687937316_649be124cc1a2eef0df3e.png!small,
1687937316_649be124cc1a2eef0df3e.png!small,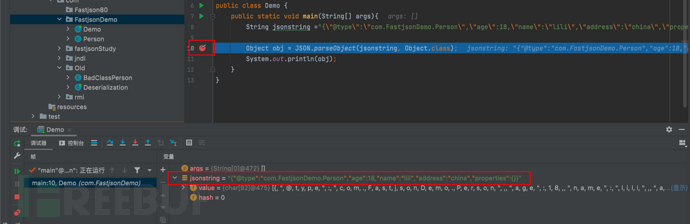 1687937342_649be13ef0c5cd18a34cb.png!small,
1687937342_649be13ef0c5cd18a34cb.png!small,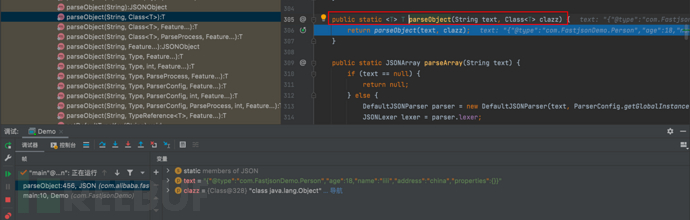 1687937363_649be1531fc289d742fdc.png!small,
1687937363_649be1531fc289d742fdc.png!small,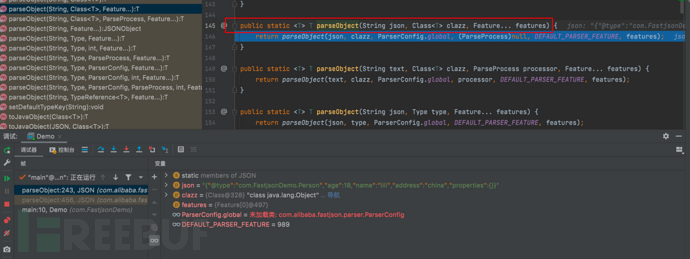 1687937388_649be16c9b766b3612ff6.png!small,
1687937388_649be16c9b766b3612ff6.png!small,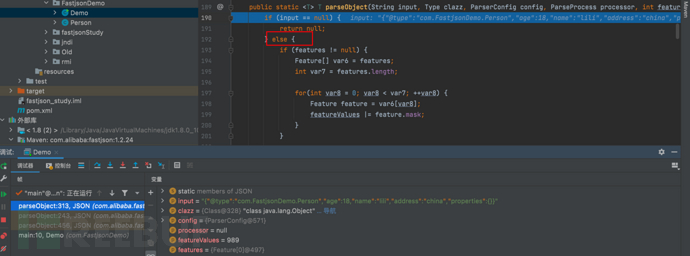 1687937405_649be17d73e3f75a24438.png!small,
1687937405_649be17d73e3f75a24438.png!small,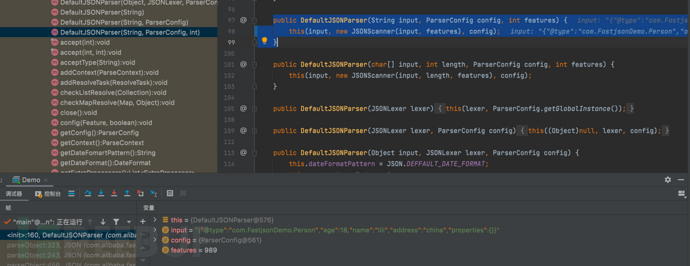 1687937426_649be192bdf7d20aea2f2.png!small,这里是使用解析器parser对JSON字符串进行解析,并将解析结果赋值给变量value。解析的目标类型由参数clazz指定,该方法返回了一个泛型类型T的对象。,
1687937426_649be192bdf7d20aea2f2.png!small,这里是使用解析器parser对JSON字符串进行解析,并将解析结果赋值给变量value。解析的目标类型由参数clazz指定,该方法返回了一个泛型类型T的对象。,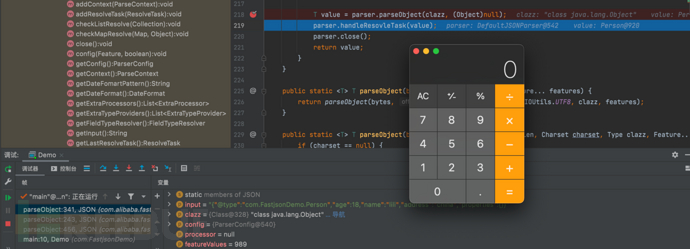 1687937451_649be1ab335e64a288968.png!small,
1687937451_649be1ab335e64a288968.png!small,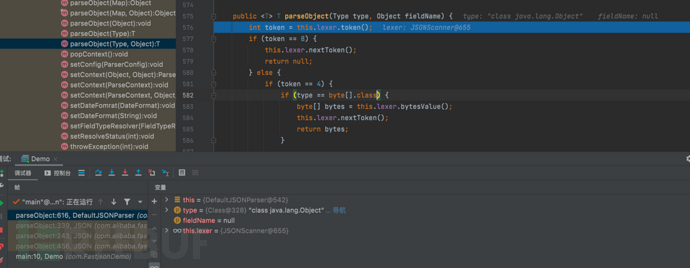 1687937468_649be1bcbd81d8fb44dfd.png!small,
1687937468_649be1bcbd81d8fb44dfd.png!small,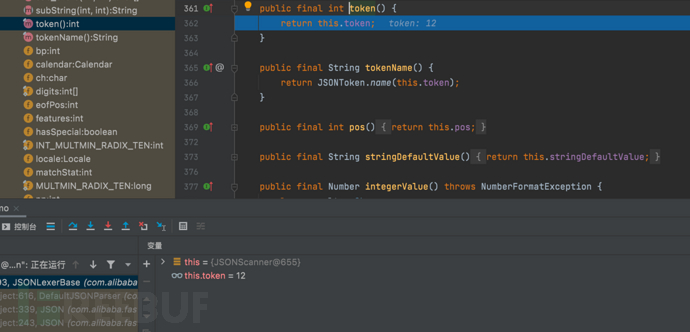 1687937487_649be1cfdddaa35c28dae.png!small,
1687937487_649be1cfdddaa35c28dae.png!small,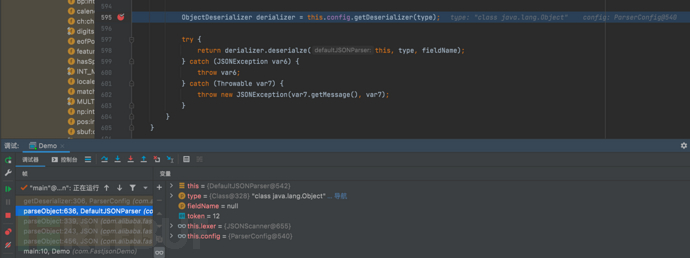 1687937506_649be1e228bb9e77e936c.png!small,
1687937506_649be1e228bb9e77e936c.png!small,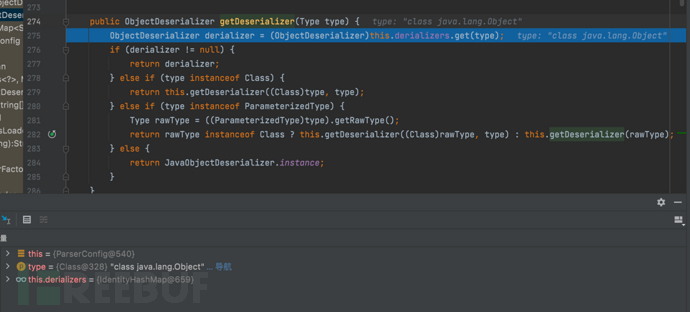 1687937526_649be1f63d5dfc461fc30.png!small,
1687937526_649be1f63d5dfc461fc30.png!small,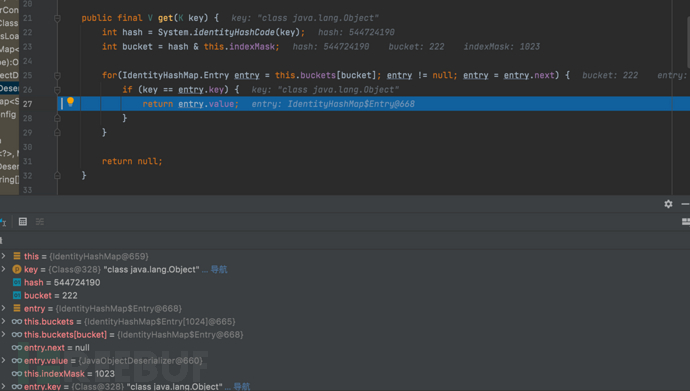 1687937545_649be2098a637e5a484fe.png!small,
1687937545_649be2098a637e5a484fe.png!small,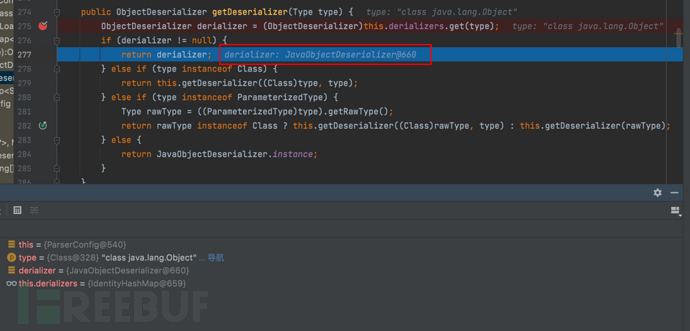 1687937561_649be21924eec7e17bac3.png!small,
1687937561_649be21924eec7e17bac3.png!small,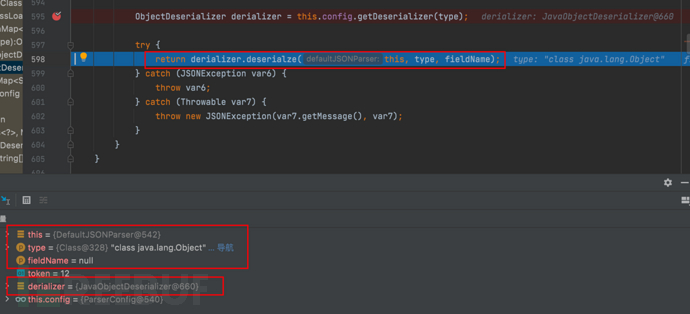 1687937578_649be22a3181634b60767.png!small,
1687937578_649be22a3181634b60767.png!small,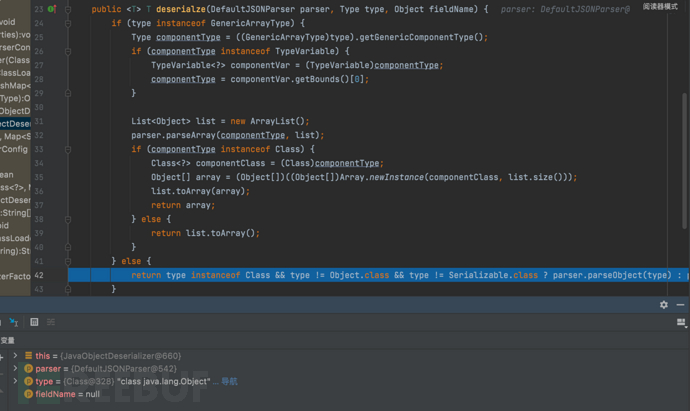 1687937595_649be23befa5d3db58b9d.png!small,
1687937595_649be23befa5d3db58b9d.png!small,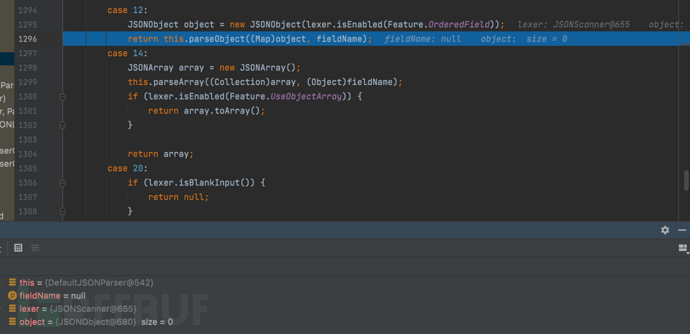 1687937621_649be2557609d8bd6b304.png!small,
1687937621_649be2557609d8bd6b304.png!small,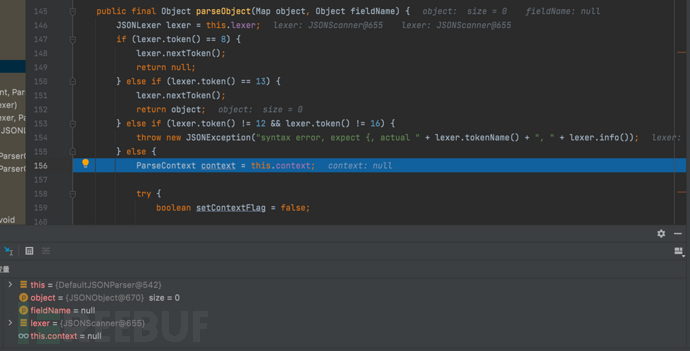 1687937638_649be2661f477f3ae3cd3.png!small,
1687937638_649be2661f477f3ae3cd3.png!small,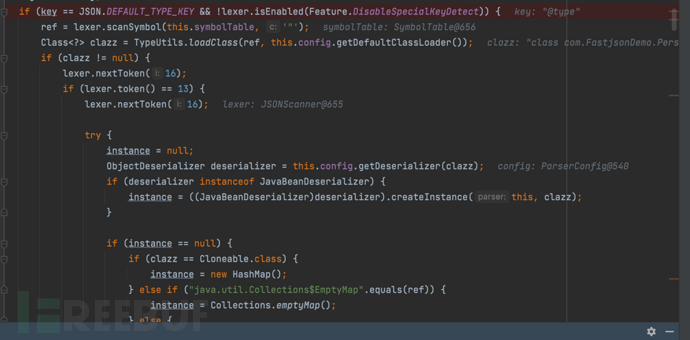 1687937659_649be27b4ae64330f43f7.png!small,
1687937659_649be27b4ae64330f43f7.png!small,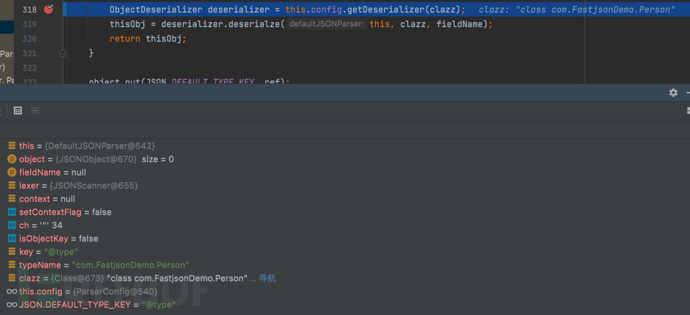 1687937707_649be2ab4ca2056ff197f.png!small,
1687937707_649be2ab4ca2056ff197f.png!small,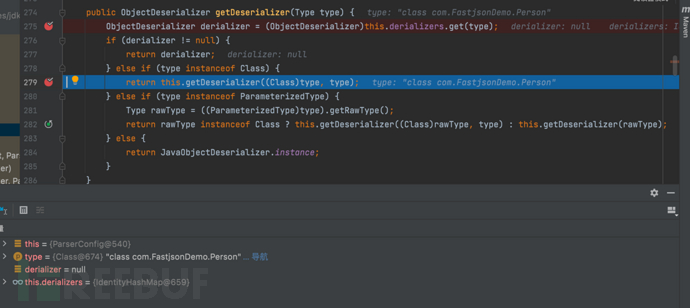 1687937723_649be2bbb78f3011e7864.png!small,
1687937723_649be2bbb78f3011e7864.png!small,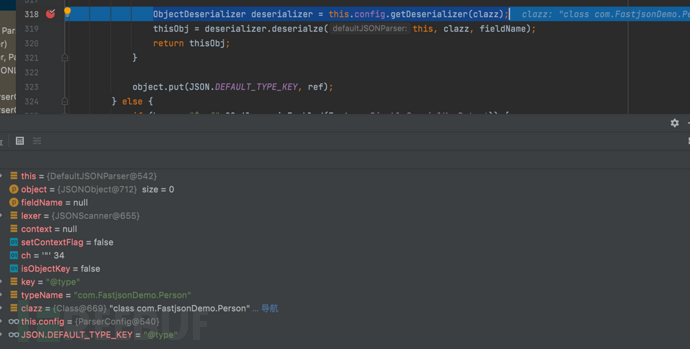 1687937739_649be2cbbdacbf8317390.png!small,
1687937739_649be2cbbdacbf8317390.png!small,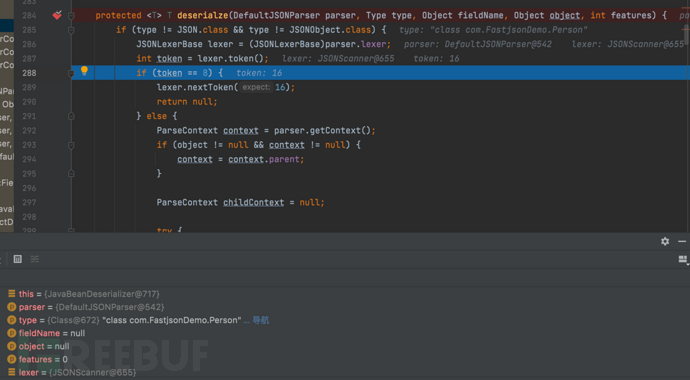 1687937757_649be2ddc1bba19ba32ea.png!small,
1687937757_649be2ddc1bba19ba32ea.png!small,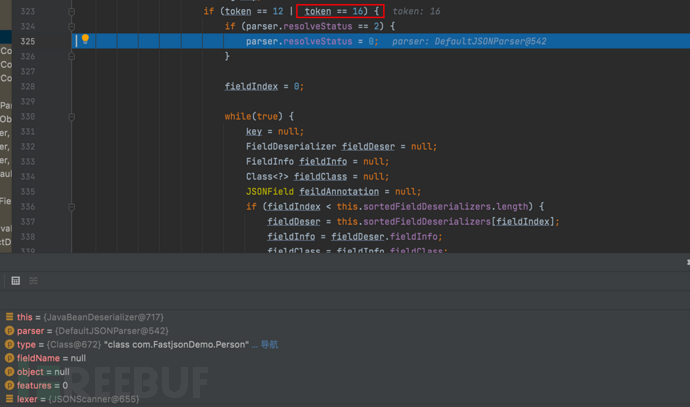 1687937783_649be2f7307263c3af1de.png!small,
1687937783_649be2f7307263c3af1de.png!small,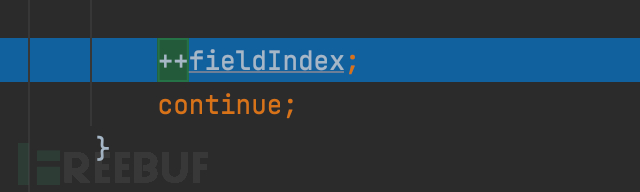 1687937809_649be311a31ab9eaef38f.png!small,
1687937809_649be311a31ab9eaef38f.png!small,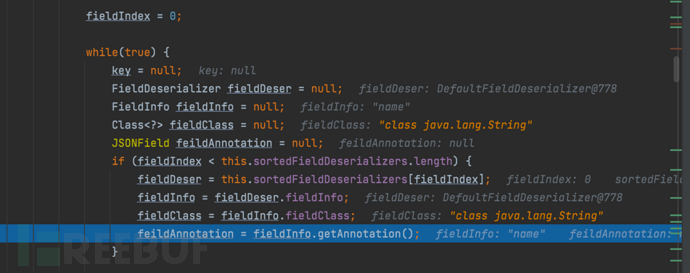 1687937832_649be32871d8efdcca30f.png!small,
1687937832_649be32871d8efdcca30f.png!small,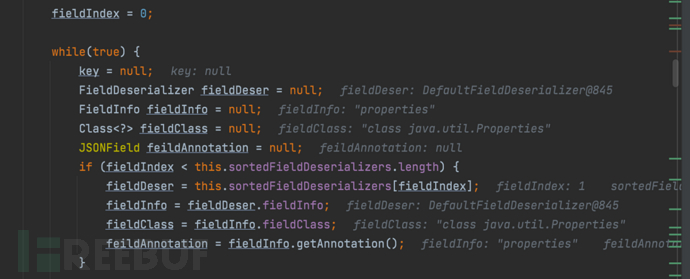 1687937864_649be3489d454e94368c4.png!small,……,
1687937864_649be3489d454e94368c4.png!small,……,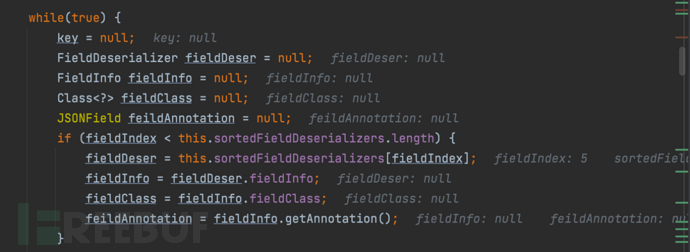 1687937882_649be35a80d859b7490fc.png!small,
1687937882_649be35a80d859b7490fc.png!small,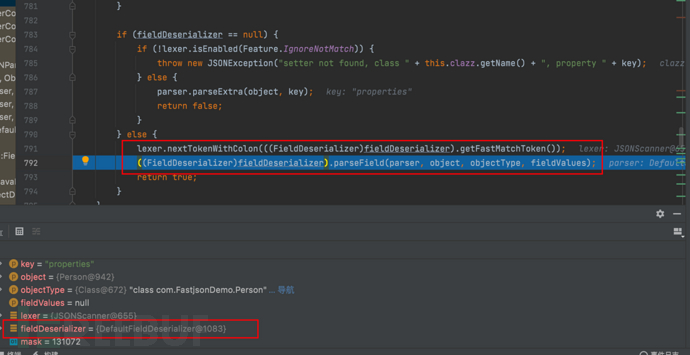 1687937908_649be374d92b4791d8cc9.png!small,
1687937908_649be374d92b4791d8cc9.png!small,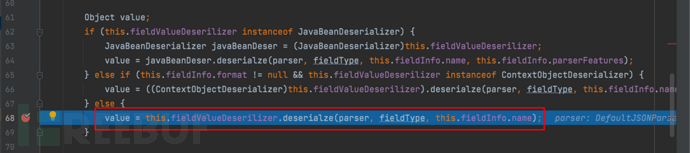 1687937927_649be3878876a960d1fb7.png!small,
1687937927_649be3878876a960d1fb7.png!small,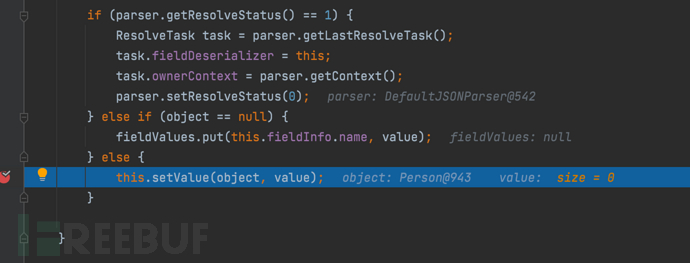 1687937955_649be3a3ca8f30bead06d.png!small,
1687937955_649be3a3ca8f30bead06d.png!small, 1687937974_649be3b66336d9ef07807.png!small,本文作者:ZavaSec, 转载请注明来自FreeBuf.COM
1687937974_649be3b66336d9ef07807.png!small,本文作者:ZavaSec, 转载请注明来自FreeBuf.COM
© 版权声明
文章版权归作者所有,未经允许请勿转载。